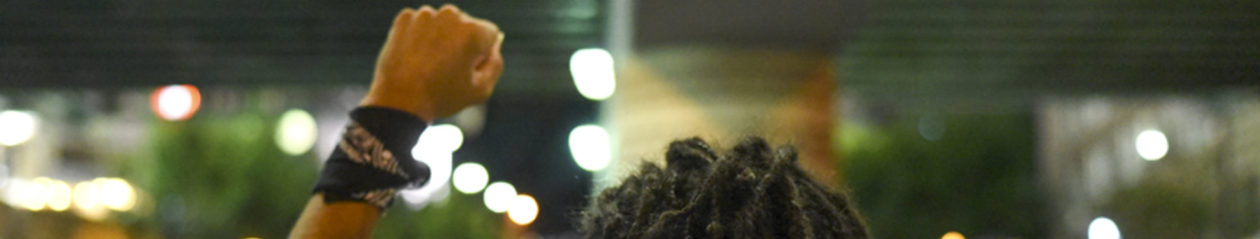Twitter is in the news for all the wrong reasons at the moment. But beyond the hack of the accounts of the great and the good, behind the scenes the microblogging site has been helping US law enforcement to track and surveil BLM protests.
Dataminr, a company that works closely with the social media platform has been using its privileged access to Twitter realtime data to inform law enforcement agencies about the latest posts of people they identify as BLM demonstrators and activists.
Both Twitter and Dataminr have previously made statements that neither would take part or assist in domestic surveillance, but according to a report by The Intercept this is clearly not the case.
Dataminr’s core business is aimed at providing corporations with a heads up on looming reputational risk issues by scanning social media to pick up signals.
Excerpt from The Intercept:
Dataminr’s Black Lives Matter protest surveillance included persistent monitoring of social media to tip off police to the locations and activities of protests, developments within specific rallies, as well as instances of alleged “looting” and other property damage. According to the source with direct knowledge of Dataminr’s protest monitoring, the company and Twitter’s past claims that they don’t condone or enable surveillance are “bullshit,” relying on a deliberately narrowed definition. “It’s true Dataminr doesn’t specifically track protesters and activists individually, but at the request of the police they are tracking protests, and therefore protesters,” this source explained.
The Intercept
Thanks Twitter: US mass surveillance… just like China?
In another report from The Intercept, journalists have uncovered how the police have ignored the real and present threat of right-wing terrorism around the BLM protests in the US, and instead preferred to pursue fictitious claims, trumpeted by Trump and others, about antifa.
The so-called Blueleaks hack has exposed the details of 700,000 cops in the US.
After the hack, Twitter shutdown the DDoSecrets site that had disseminated information about the Blueleaks hack. The Reddit sub – r/blueleaks has also been banned.
The leaked data dates from 2007 to June 14, 2020, so include much of the protests that took place following the murder of George Floyd by police.
Much of the information in the leaks has come from so-called Fusion centres set up post 9/11 with the purpose of enabling different state and Federal law enforcement agencies to share information.
Some of the hacked websites also included those where law enforcement collaborates with corporations in various guises, such as the Energy Security Council.
Many hacked sites also included data from the high-intensity drug trafficking area program (HIDTA).
And finally another bunch of websites were membership-only police officer associations of one type or another.
Of particular interest were the many instances of SAR reports uncovered – Suspicious Activity Reports.
One such SAR concerned a student seeking pro bono legal aid assistance from a law firm.

A racist lawyer saw it and contacted law enforcement.

“PLEASE SEE THE ATTACHED SOLICITATION I RECEIVED FROM AN ANTIFA TERRORIST WANTING MY HELP TO BAIL HER AND HER FRIENDS OUT OF JAIL, IF ARRESTED FOR RIOTING,” he typed into an unhinged letter, in all-caps, that he mailed to the Marin County District Attorney’s office, just north of San Francisco.
He explained that he was remaining anonymous because he “CANNOT RISK THIS PIECE OF SHIT ANTIFA […] FILING A BAR COMPLAINT AGAINST ME,” and warned that “THE SAN FRANCISCO PUBLIC DEFENDERS WILL VIGOROUSLY DEFEND THESE TERRORISTS.” He ended his letter, “HAPPY HUNTING.”
Instead of throwing the lawyer’s communication in the garbage, it was uploaded to the local fusion centre as useful intelligence.
This is one example of an estimated 1,200 commmunity-submitted SARs.
Other SARs were similarly racist.
Again, the full story at The Intercept.
Please consider donating to The Intercept so they keep up with their brilliant investigative journalism.